Historical Context of Layered Security
The onion model emerged during the growth of enterprise IT when organizations responded to new threats by adding new defensive layers. Each incident or compliance requirement led to another perimeter or middleware control. While effective in the short term, this layered approach produced patchwork systems with overlapping functionality, inconsistent policies, and gaps that attackers could exploit.
The Onion Model and Its Vulnerabilities
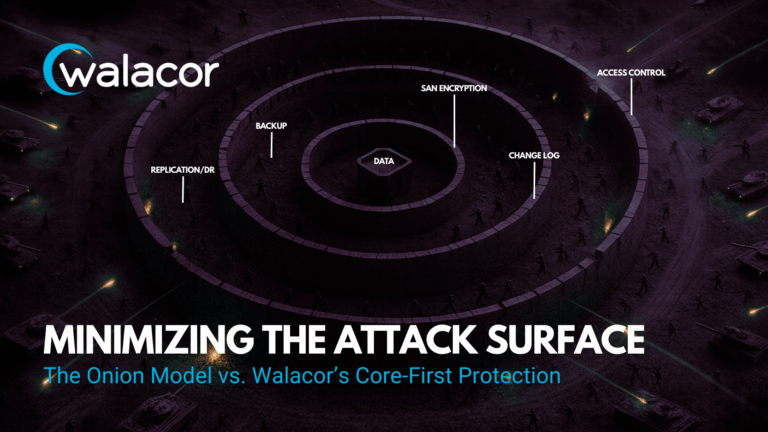
The traditional “onion model” of cybersecurity layers defenses concentrically around a central database. Each layer is intended to provide a barrier against intrusion, but the cumulative effect is often an expanded and more complex attack surface. From the inside out, the layers typically include:
- Database (Data) – the core asset containing customer records, financial transactions, intellectual property, logs, and other sensitive information.
- Schema & Validation – enforcement of data formats, constraints, and integrity checks designed to prevent malformed or malicious inputs from reaching the core.
- Application Logic & APIs – business rules and access methods that determine how applications interact with the database, often exposing numerous interfaces.
- Access Controls & Identity (IAM) – authentication and authorization services (passwords, tokens, SSO, MFA) that regulate who can reach protected resources.
- Encryption Services – cryptographic mechanisms for protecting data at rest and in transit, including key management, TLS/SSL, and disk-level encryption.
- Firewalls / Perimeter Security – network boundary defenses, intrusion detection systems, packet filtering, and monitoring services designed to repel external threats.
Why the Attack Surface Expands
While each layer aims to protect the core, collectively they create new opportunities for exploitation:
- Integration Points – every interface or protocol boundary becomes a seam that can be misconfigured or attacked.
- Configuration Complexity – with more interdependent systems, administrators must manage extensive policy sets and security rules, increasing the likelihood of mistakes.
- Expanded Targets – each layer (firewalls, IAM, middleware, encryption appliances) presents its own vulnerabilities, requiring constant patching and monitoring.
- Dependency Chains – the failure of a single outer system can cascade inward, leaving the core exposed despite the presence of other controls.
In practice, adding more layers often enlarges the attack surface instead of shrinking it. Attackers exploit this complexity, probing for the weakest link among numerous entry points.
Operational Cost of a Typical Attack Surface
Beyond theoretical weaknesses, a large attack surface carries real operational costs. Tool sprawl burdens administrators with dozens of systems to configure and maintain. Overlapping monitoring layers generate alert fatigue, obscuring genuine threats. Security budgets become diluted, funding maintenance of redundant defenses rather than reinforcing the integrity of the data itself.
Modern Threat Landscape
Today’s adversaries exploit weaknesses that layered defenses cannot easily address. Lateral movement bypasses layers once attackers are inside a network. Supply chain compromises enter through trusted applications, neutralizing perimeter filters. Zero-day exploits render outer walls ineffective overnight. Core-first security, with protection embedded at the data level, ensures confidentiality and integrity even in the face of these modern tactics.
Architectural Simplicity as Security
Simpler architectures are inherently more secure. Each removed integration point reduces the trusted computing base and the probability of misconfiguration. By embedding protections directly into the data layer, Walacor collapses overlapping controls, producing a system that is easier to audit, verify, and trust. This simplicity is itself a security multiplier.
The Core-First Alternative
A core-first security model inverts the paradigm by embedding protections at the data layer itself rather than relying primarily on external systems:
- Record-Level Encryption and Validation – each data element carries its own cryptographic safeguards, ensuring confidentiality and authenticity.
- Immutable Integrity Proofs – cryptographic hashes and proofs guarantee that tampering is detectable, independent of outer defenses.
- Minimized Trust Dependencies – fewer external layers are required for assurance, reducing the number of systems that must be defended and configured.
- Resilience Under Breach – even if outer controls fail, the data itself remains cryptographically protected and resistant.
This approach shrinks the attack surface by concentrating security at the point of greatest value: the data. Instead of expanding outward with additional complexity, it reduces potential vectors for compromise.
Walacor and Core-First Protection
Walacor implements the core-first philosophy by embedding immutability, cryptographic enforcement, and schema validation directly into the data layer. Rather than building outward layers that expand the attack surface, Walacor collapses unnecessary perimeter complexity and anchors protection where it cannot be bypassed: the data itself.
- Data-Level Cryptography – each record is encrypted and bound to proofs of authenticity, eliminating reliance on external encryption appliances.
- Immutable Storage – records are tamper-evident at the core, reducing the need for overlapping monitoring systems.
- Integrated Validation – schema and policy checks occur at write-time, blocking invalid or hostile data without middleware add-ons.
- Shrinking the Attack Surface – because Walacor renders many outer layers redundant, there are fewer interfaces to defend, fewer seams to misconfigure, and fewer targets for attackers.
Walacor demonstrates that the most effective way to minimize the attack surface is to concentrate defenses in the core, ensuring data integrity and confidentiality regardless of the state of external systems.
Agents, AI, and the Attack Surface
The emergence of intelligent agents and AI-driven systems adds a new dimension to the attack surface discussion. Agents interact with data across multiple contexts—querying, transforming, and making autonomous decisions. In a traditional layered model, each of these interactions multiplies the integration points and potential vulnerabilities. Malicious prompts, poisoned training data, or compromised connectors can all bypass outer defenses to reach sensitive information.
A core-first model directly addresses this risk. By cryptographically securing and validating data at the record level, Walacor ensures that even AI agents cannot be tricked into handling falsified or tampered records. Every data element carries its own assurance, creating a trustworthy substrate for automated reasoning and machine learning pipelines. In this way, AI becomes a consumer of verifiable data rather than a potential vector for hidden compromise, aligning intelligent agents with the same guarantees that protect human operators.
Forward-Looking Implications
A core-first approach lays the groundwork for enduring benefits. Immutable, verifiable data strengthens sovereignty in federated and multi-cloud environments. Compliance becomes easier, as audit trails and integrity proofs are inherent to the system rather than bolted on. This architecture future-proofs sensitive systems, ensuring resilience against evolving threats.
Reinforcing the Core-First Premise
The onion model reflects a reactionary philosophy that often results in excessive complexity and a sprawling attack surface. A core-first strategy simplifies the architecture by embedding protection directly into the data layer, eliminating unnecessary exposure and ensuring that sensitive information remains secure even in hostile conditions.